Executive Summary
The Client is a passionate start-up dedicated to the empowerment of educators. They honor them by providing institutions with innovative solutions that radically revamp the way that teachers, parents and students interact. They wanted to secure and manage their Application infrastructure on the AWS Cloud.
About The Customer
Our Client believes in enriching the next generation, granting them the quality education and values that are vital to success in the world today and we believe that such life changing value and growth can only be imparted when teacher-student education is of utmost important. They are currently deeply involved in the education sector, and work closely with official agencies on the next wave of smart solutions in Singapore, a holistic management system that brings intuitive efficiency to daily operations.
Customer Challenge
Web applications are vulnerable to a variety of attacks. These attacks include specially crafted requests designed to exploit a vulnerability or take control of a server; volumetric attacks designed to take down a website; or bad bots and scrapers programmed to scrape and steal web content.
The Client had their web application already hosted on AWS. However, they infrastructure was not optimized and not at all secure. They were using AWS services such as Code Build, Code Deploy, Code Commit to deploy the code on to the servers.
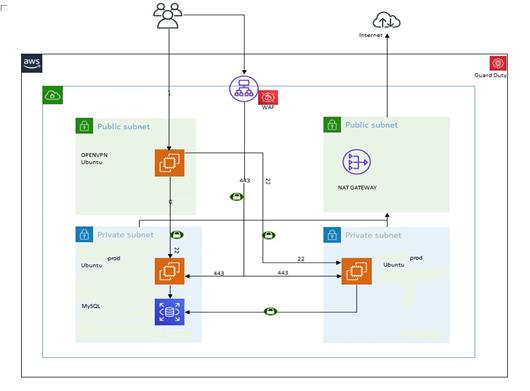
The access to the applications was through a load balancer and CloudFront with no level of protection whatsoever.
Why AWS
The Client already had their infrastructure on AWS and wanted a partner to optimize their infrastructure around all the five pillars of the well-architected framework.
As part of this engagement, Aspire NXT proposed the optimizations around all the pillars thus, including security. We leveraged multiple AWS Security Services to protect their AWS environment and the resources in it.
To facilitate the continuous build and deployment environment in AWS, the Client chose to work with Aspire NXT, an IT services provider that is part of the AWS Partner Network (APN).
Why AWS
Partner Solution
After an initial assessment, Aspire NXT helped the Client to:
- Setup a secured environment using WAF for protection against common web attacks.
- We attached AWS WAF to CloudFront CDN and the Load Balancer wherein a request comes from the outside, it is filtered by WAF before allowing access to the CDN/Load Balancer
- We enabled Logging for WAF to periodically review the logs and identify any possible optimizations and custom rules which can be suggested to the Client.
- A web application firewall is optimized to protect their web application and it is deployed analyze bi-directional web-based (HTTP/HTTPS) traffic – detecting and blocking anything malicious.
- It works as a shield or proxy between the internet and their web application thus protecting the server from exposure.
- During periodic reviews we realized that an average request going through WAF are 200K/day.
WAF is configured with the following rules to protect the Client web applications against various attacks:
- SQL Injection
- PHP Injection
- Known bad inputs
- IP Reputation Lists
- Anonymous IP Lists
- Core Rule set- include OWASP Top 10 protection
- Admin Protection Rule set
- Custom Rules (HTTP Floods rate-based control, HTTP referrer to check for the referrer header and only allow APIs from the client application)
Results and Benefits
The WAF differs from a regular firewall as it is optimized to filter the web applications while regular firewalls serve as a safety gate between servers.
For our client:
- It inspects the web traffic, and prevents common attacks stemming from variety of reasons like misconfigurations, bad practices, vulnerabilities, etc.
- It helps protect the web application and APIs against common web exploits that may affect availability, compromise security, or consume excessive resources.
- It gives control over how traffic reaches the application by enabling them to create security rules that block common attack patterns.
- Some other benefits are like agility to protect against attacks, ease of use, improved visibility over web traffic, etc.




